Service mesh: Observe and secure your mesh with metrics
Everything you need to coordinate microservices in a service mesh with powerful monitoring and management tools like Istio and Kiali.

What is a service mesh?
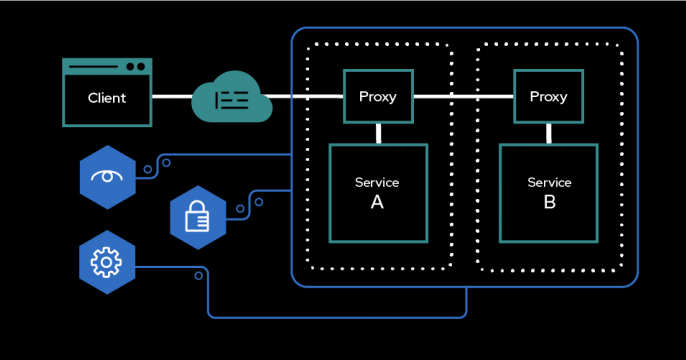
A service mesh is a combination of tooling and infrastructure that manages communication and interaction between individual services. The service mesh disconnects the network needs from each microservice so that each service can be observed and monitored across the whole system. Service meshes can also be applied to individual architectures that require multiple services to communicate.
How do service meshes help developers?
Service meshes are ideal for development teams that need to access services through network interfaces and protocols and well-defined management of service-to-service communication. They deliver advanced traffic control, security, resilience, and observability for cloud-native apps and enable standardization across service interactions. By allowing applications to offload these capabilities from application-level libraries, service meshes provide developers with quicker deployments and deployment cycles.
You can change Istio settings to invoke fault injection or support a Canary Deployment or anything else Istio supports, all while never touching your application source code. For example, let's say you want to direct all web traffic from your largest customer (Foo Corporation) to a new version of your website.
You may decide to do this by simply creating an Istio Route Rule that searches for @foocorporation.com in their user ID and directs them appropriately. To the rest of the world, this change would be transparent. Meanwhile, you can test your new software.

Service Mesh communities are focused on improving the ease of adoption and reducing the resource requirements to run a service mesh. This can best be seen in new implementations that remove the need for sidecar proxies.
Examples of sidecar-less service meshes include:
- Istio’s ambient mode: An Istio data plane mode that uses two levels of proxies to remove the need for sidecar proxies. The ZTunnel is a per-node lightweight proxy that provides layer 4 telemetry and mutual TLS encryption between services, including certificate management. Waypoints are independently scalable Envoy proxies that provide layer 7 telemetry and traffic management features. Put together, this topology significantly reduces resource usage compared to a sidecar-based service mesh, while providing a comparable feature set.
- Cilium: This open-source project heavily utilizes eBPF to provide some service mesh capabilities without requiring sidecar proxies.

Explore best practices for eBPF application development on Linux, including...

Get started with the bpfman eBPF manager with this tutorial. You'll see how...
Discover why Istio ambient mode is better than the traditional sidecar model...
Manage network communications with OpenShift Service Mesh
As your applications evolve into collections of decentralized microservices, monitoring and managing the network communications and security among those multiple services, is challenging. Red Hat OpenShift Service Mesh offers a uniform way to connect, manage, observe, and provide security for microservices-based applications, that includes behavioral insight into and control of the networked microservices in your service mesh.
Follow along to configure and run a demo application under OpenShift Service Mesh. Discover how the service mesh controls the application from a conceptual point of view, then walk through the steps to get the application up and running under an OpenShift Service Mesh.
Latest service mesh articles

Discover why Istio ambient mode is better than the traditional sidecar model...

Learn how to implement the Kubernetes Gateway API 1.0 feature on Red Hat...

Explore OpenShift Service Mesh's multi-cluster features and learn how to...

Find out what's new for developers in Red Hat OpenShift 4.15. Access Tekton...

Learn how to get the most from OpenShift Service Mesh tracking and monitoring.

Here are the most popular Kubernetes resources of 2023, featuring a guide to...

Explore new features in Red Hat OpenShift 4.14, including enhanced security...

Explore the differences between Red Hat OpenShift Service Mesh and Red Hat...
DevNation Deep Dives: Istio service mesh
Learn about the fundamentals of Istio Service Mesh in these new online deep dives.



